CVE-2023-43457 - Broken Access Control (BAC)
About the Application
This Service Provider Management System v.1.0 is a sort of Content Management System (CMS) that is built specifically for companies that provide different services. The project is a company website that allows the management to dynamically manage the site information and other data on the front end. This project has 2 modules which are the Public and Management site.
The Management Site is the side of the system where accessible to the company staff or system-registered users only. On this site, users are required to log in with their valid system credentials to gain access to the features and functionalities. Users have 2 different roles which are the Administrator and the Staff. The Administrator users have the privilege to manage and access all the features and functionalities of the said site while the Staff users only have limited permissions. Here, system users can manage the list of services that their company provided. They can also update the dynamic page content of the public website on this side.
Vulnerability Description
Privilege Escalation in Service Provider Management System v.1.0 allows a remote attacker to gain privileges via the ID parameter in the /php-spms/admin/?page=user/manage_user&id=9 endpoint.
Vulnerable Code
Filename: /php-spms/admin/user/manage_user.php
Vulnerable Endpoint: /php-spms/admin/?page=user/manage_user&id=9
Vulnerable Parameter: id
Code:
1
2
3
4
5
6
7
8
9
10
11
12
<?php
if(isset($_GET['id'])){
$user = $conn->query("SELECT * FROM users where id ='{$_GET['id']}' ");
foreach($user->fetch_array() as $k =>$v){
$meta[$k] = $v;
}
}
?>
<?php if($_settings->chk_flashdata('success')): ?>
<script>
alert_toast("<?php echo $_settings->flashdata('success') ?>",'success')
</script>
The code checks if the id parameter is set in the URL but does not verify whether the authenticated user has the appropriate permissions to access the user data associated with that id. It assumes that anyone with the id parameter can access any user’s information. This oversight creates a security vulnerability known as ‘Broken Access Control (BAC), especially concerning the id parameters.
Broken Access Control is a security vulnerability in web applications and systems where proper access controls are not enforced, allowing unauthorized users to gain access to resources, perform actions they shouldn’t, or manipulate the system in unintended ways. Examples include inadequate authorization checks, missing authentication, direct object reference, overly permissive permissions, and failure to revoke access. To mitigate this issue, applications should implement strong access controls, enforce authentication and authorization rigorously, follow least privilege principles, and regularly test for and address potential access control problems.
Impact of Broken Access Control
The exact reasons for the impact of broken access control in a web application or system include:
Unauthorized Access: Broken access control allows unauthorized users to gain access to resources and functionality that should be restricted to certain users or roles.
Data Exposure: When access controls are not properly enforced, sensitive data can be exposed to users who shouldn’t have access, leading to data leaks and breaches.
Data Manipulation: Attackers can alter, delete, or insert data into the system, potentially causing data corruption and fraudulent activities.
Attack Scenario
- Go to
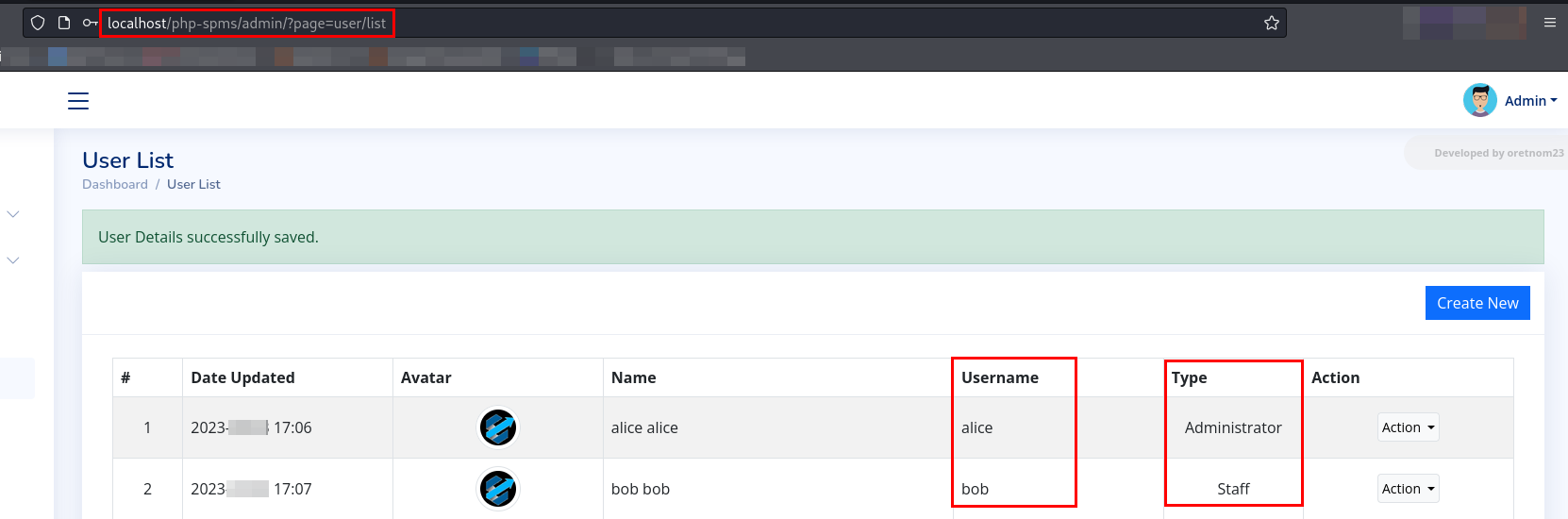
http://localhost/php-spms/admin/?page=user/listand create 2 user,aliceasadministratorandbobasstaff.
- Let’s view both user and notice the
idassigned to each user.
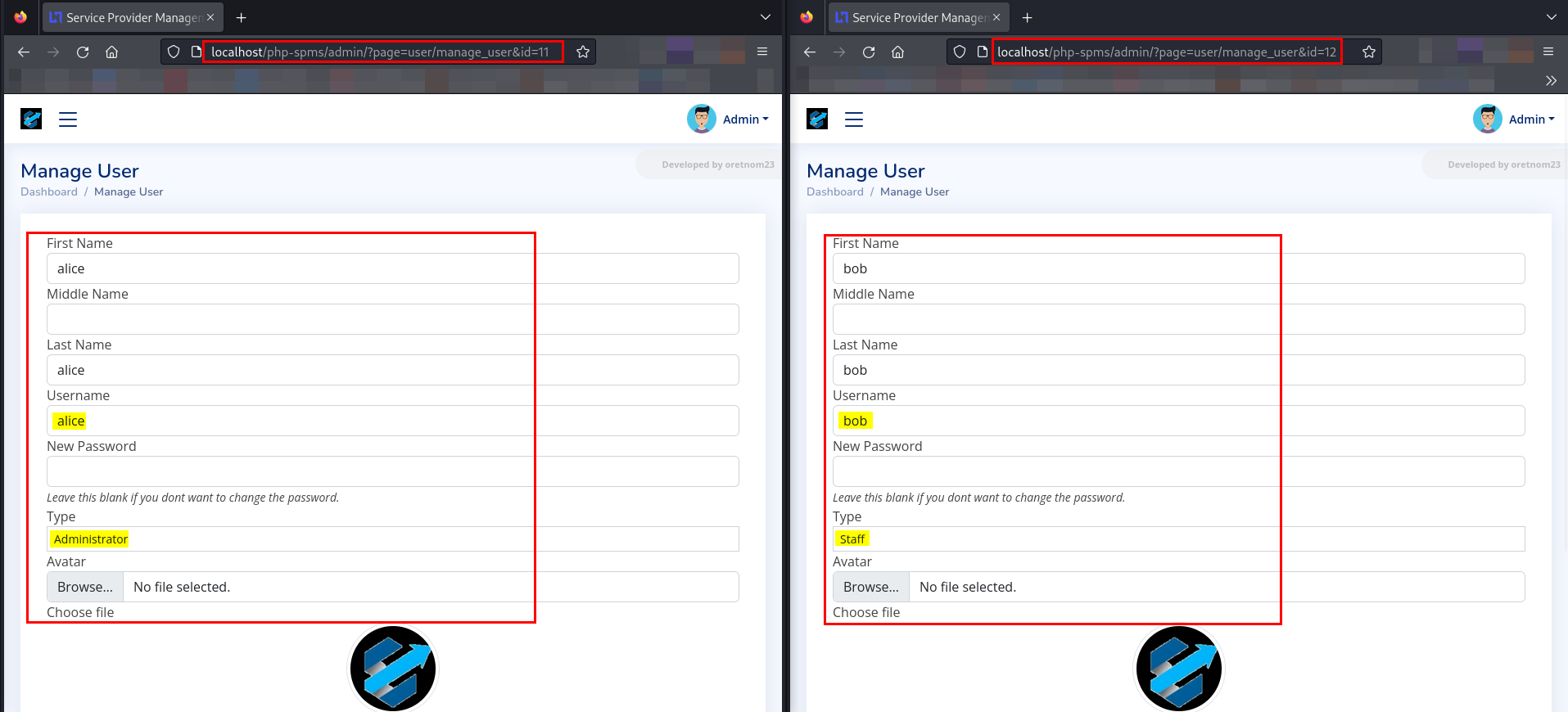
- Let’s login as
bobwho is astaffand visit the URLhttp://localhost/php-spms/admin/?page=user/manage_user&id=12
- Let’s change the
idvalue from 12->11 and see if we can access the details of useralice.
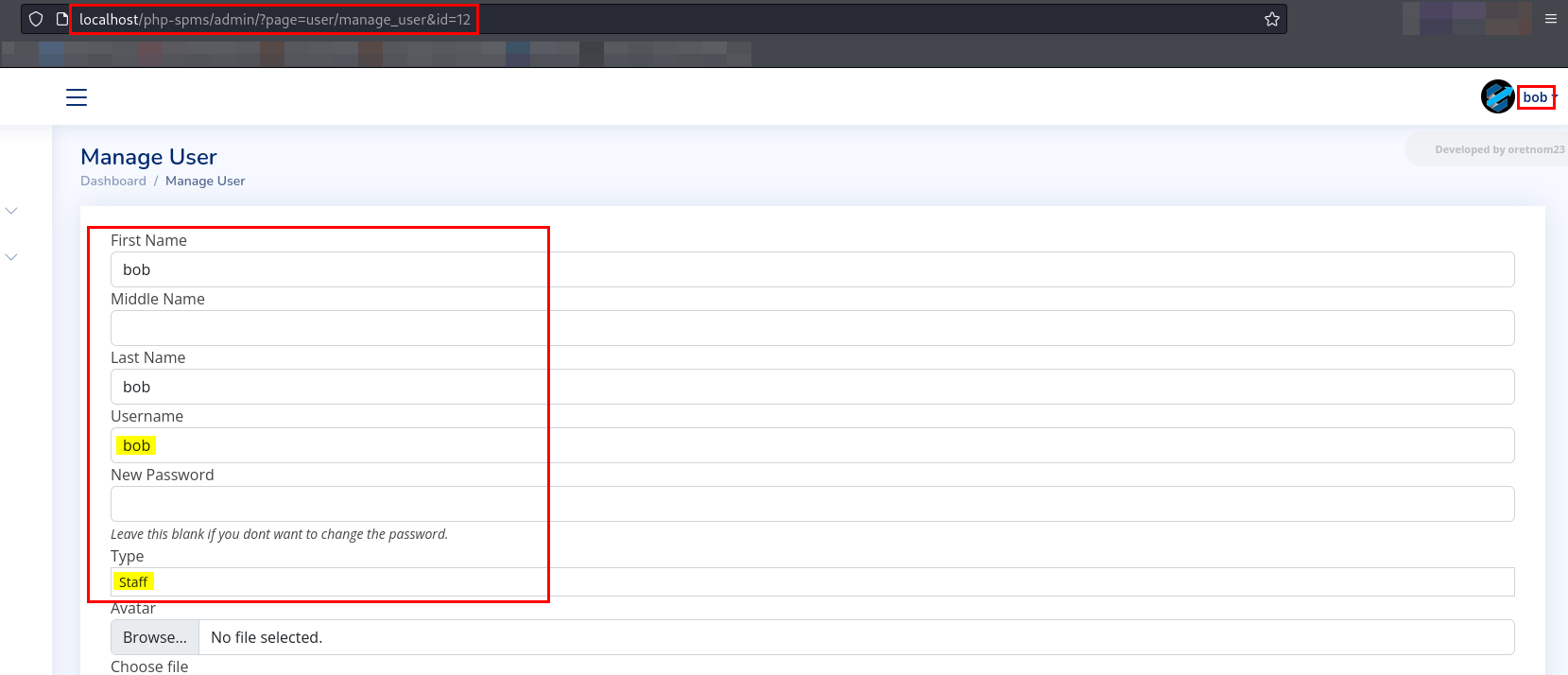
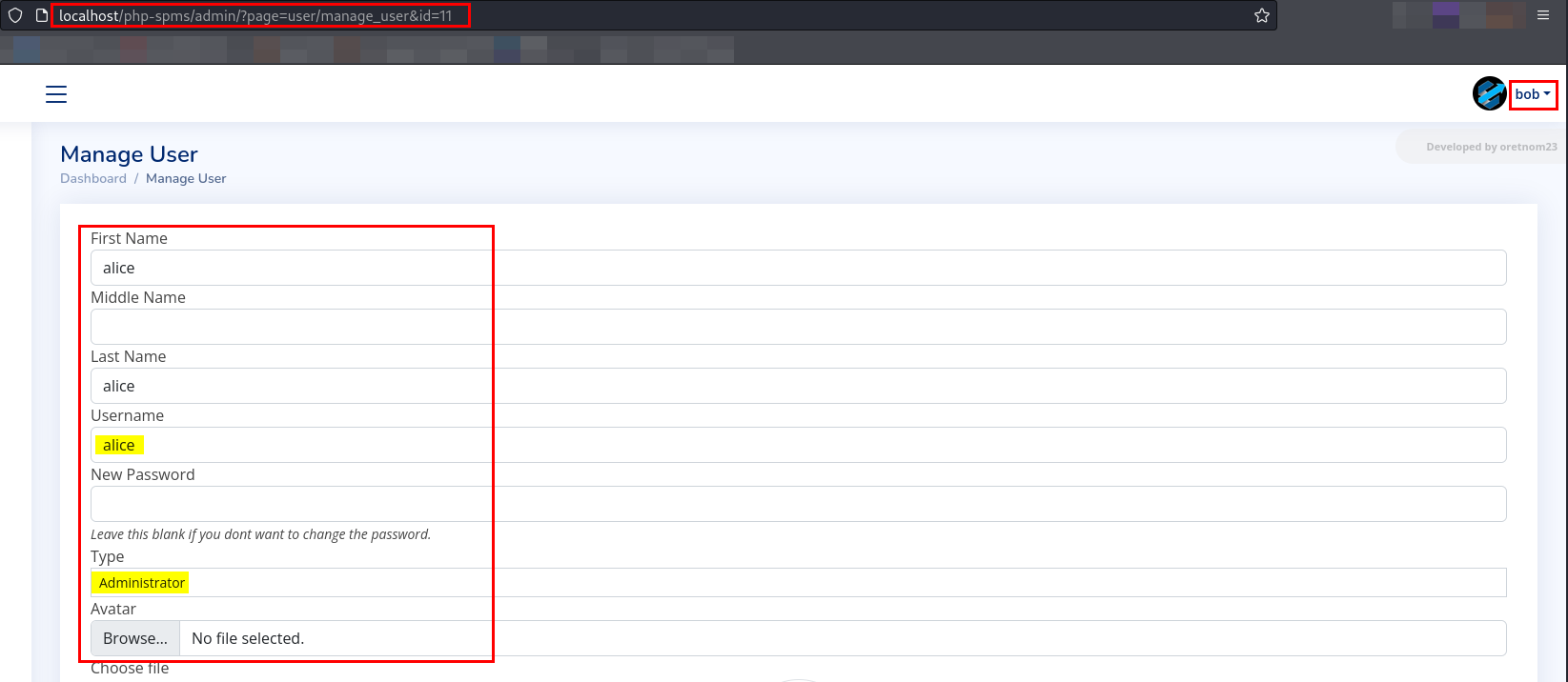 Alice’s detail is accessible by bob
Alice’s detail is accessible by bob
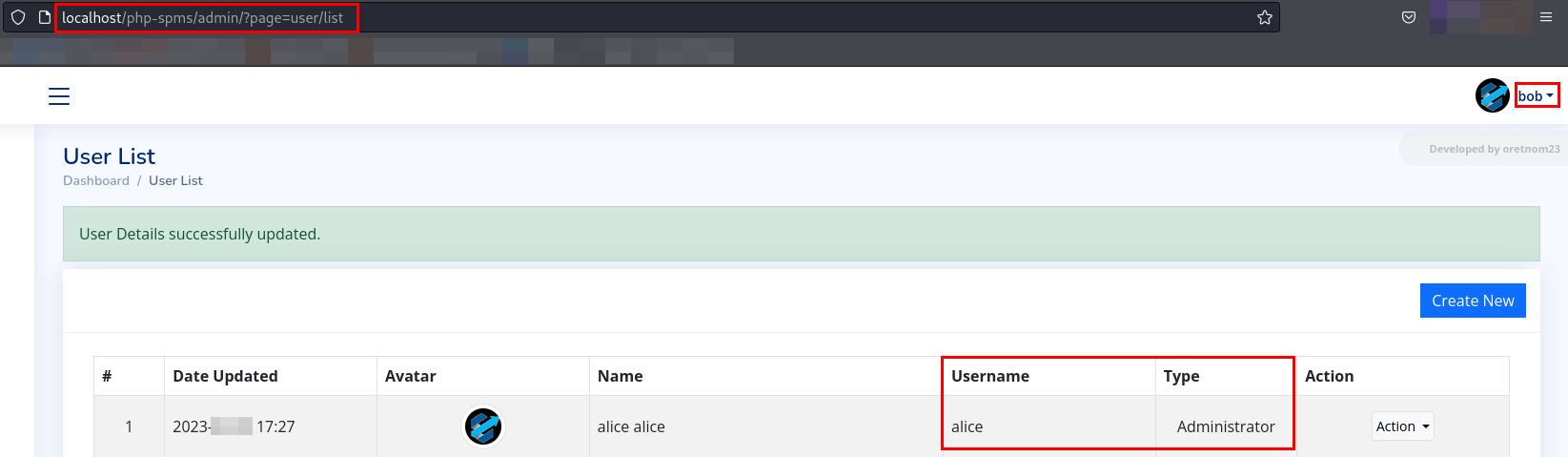
- We can able to view the information of
alice, let’s try to change the password ofalice.
Remediation
Remediating broken access control vulnerabilities is crucial to secure your web application or system. To address these vulnerabilities effectively, follow these remediation steps:
Implement Proper Authentication and Authorization: Ensure that your application uses strong authentication mechanisms to verify user identities. Use multi-factor authentication (MFA) for added security. Implement fine-grained authorization controls based on user roles and privileges. Users should only have access to resources and actions they are authorized to use.
Access Control Lists (ACLs) or Role-Based Access Control (RBAC): Implement ACLs or RBAC to define and manage access permissions for users and resources. This helps maintain a clear and structured access control policy.
Secure Session Management: Implement secure session management to ensure that session tokens are generated securely, invalidated after logout or inactivity, and protected against session fixation attacks.
That’s all in this writeup.
Thanks for reading this far. If you enjoyed the writeup, do support me here.